Maximizing VPN Benefits & Advanced Online Privacy: A Deep Dive for the Discerning Web User
In 2025, the digital world is more interconnected, dynamic, and, unfortunately, more vulnerable than ever before. Every click, every search, and every online interaction leaves a digital trail that can be collected, analyzed, and even exploited. From pervasive trackers monitoring your Browse habits to the constant threat of data breaches and government surveillance, the need for robust digital privacy and online security has never been more critical.
Many of us have adopted a Virtual Private Network (VPN) as our first line of defense, recognizing its power to hide our IP addresses. However, for the discerning web user, merely “hiding” is no longer enough. The landscape of online threats is constantly evolving, and so too must our approach to advanced VPN use. This comprehensive guide will go beyond the basics, exploring the full spectrum of VPN benefits, diving into sophisticated features, and introducing complementary tools essential for achieving unparalleled online anonymity in today’s complex digital age. Prepare to take full control of your digital life.
Beyond Basic Anonymity: Unlocking Your VPN's Full Potential
A VPN is far more than just an IP address masker; it’s a versatile security and access tool. By encrypting your internet connection and routing it through a server in a location of your choosing, it opens up a world of benefits that extend well beyond simple anonymity.
Secure Public Wi-Fi Connections: Picture this: you’re catching up on emails at a coffee shop or waiting for a flight at the airport, connected to free public Wi-Fi. What you might not realize is that these networks are often unsecured, making your data vulnerable to snoopers, hackers, and even malware injection. An unsecure public Wi-Fi connection is an open invitation for trouble. A VPN acts as your personal digital bodyguard, encrypting all your data before it leaves your device. This creates a secure, impenetrable tunnel, protecting your sensitive information – from banking details to private messages – from interception by malicious actors on the same network. It’s an essential safeguard for anyone on the go.
Bypassing Geo-Restrictions & Accessing Global Content (Ethical Use): Ever tried to watch a show on a streaming service, only to be met with “Content not available in your region”? This is geo-blocking, a common practice based on your geographical location. A VPN allows you to change your virtual location by connecting to servers in different countries. This means you can ethically bypass geo-blocking and access content (like streaming libraries, news, or even region-specific online shops) that would otherwise be unavailable. It’s like having a digital passport that lets you explore the internet without artificial borders.
Evading ISP Throttling & Data Monitoring: Your Internet Service Provider (ISP) acts as the gateway to the internet, meaning they can see your unencrypted online activities. Some ISPs log your Browse history, and in certain regions, they might even throttle your bandwidth for specific services (e.g., streaming, gaming) to manage network traffic. When you use a VPN, your internet traffic is encrypted, rendering it unreadable to your ISP. This not only prevents them from monitoring your activities but also makes it significantly harder for them to prevent ISP tracking or selectively ISP throttling VPN your connection based on the content you’re accessing. You regain control over your bandwidth and privacy.
Enhanced Torrenting/P2P Safety & Privacy: Peer-to-peer (P2P) file sharing, often associated with torrenting, carries inherent privacy and legal risks if done without proper protection. Your IP address is visible to everyone in the swarm, potentially exposing you to unwanted attention from copyright holders or malicious entities. A VPN becomes crucial for secure torrenting, as it hides your true IP address, making your activity anonymous and significantly reducing privacy and legal concerns during file sharing.
Potentially Saving Money on Online Shopping & Flights: Did you know that prices for flights, hotels, and even some online subscriptions can vary based on your geographical location? Airlines and e-commerce sites sometimes use dynamic pricing. By using a VPN to change your virtual location, you can sometimes discover different pricing tiers, potentially leading to significant online shopping discounts or VPN for cheaper flights. It’s a clever trick for the savvy shopper.
Advanced VPN Features: Mastering Your Privacy Toolset
While basic VPN functions are powerful, a premium VPN offers a suite of advanced features that can truly elevate your security and give you granular control over your online privacy. Don’t just use a VPN; master it.
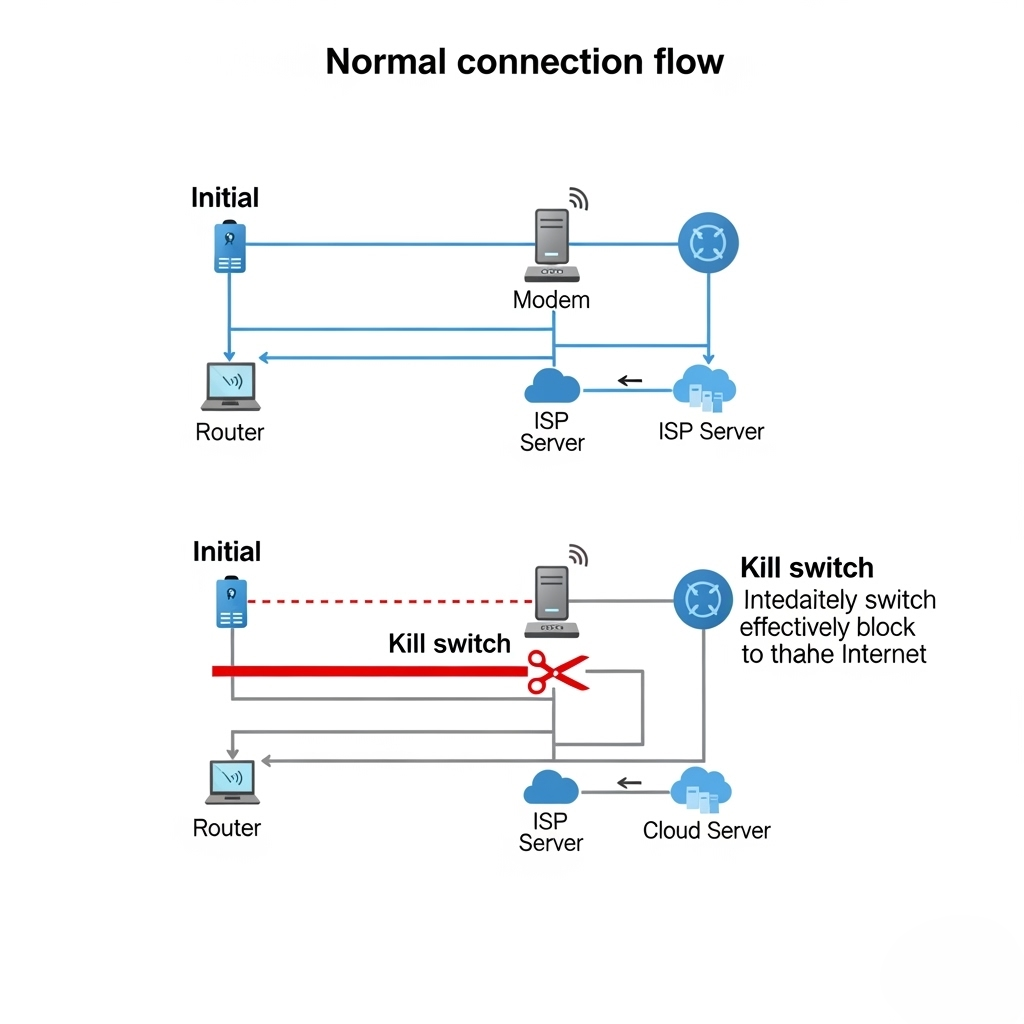
The Indispensable Kill Switch: Imagine your VPN connection suddenly drops due to a network glitch or server issue. Without a kill switch, your device automatically reverts to your unprotected internet connection, instantly exposing your true IP address and online activity. A VPN kill switch is a critical security feature that automatically disconnects your device from the internet if the VPN connection drops unexpectedly. It’s vital for preventing IP leaks and ensuring continuous privacy, acting as an always-on guardian for your connection.
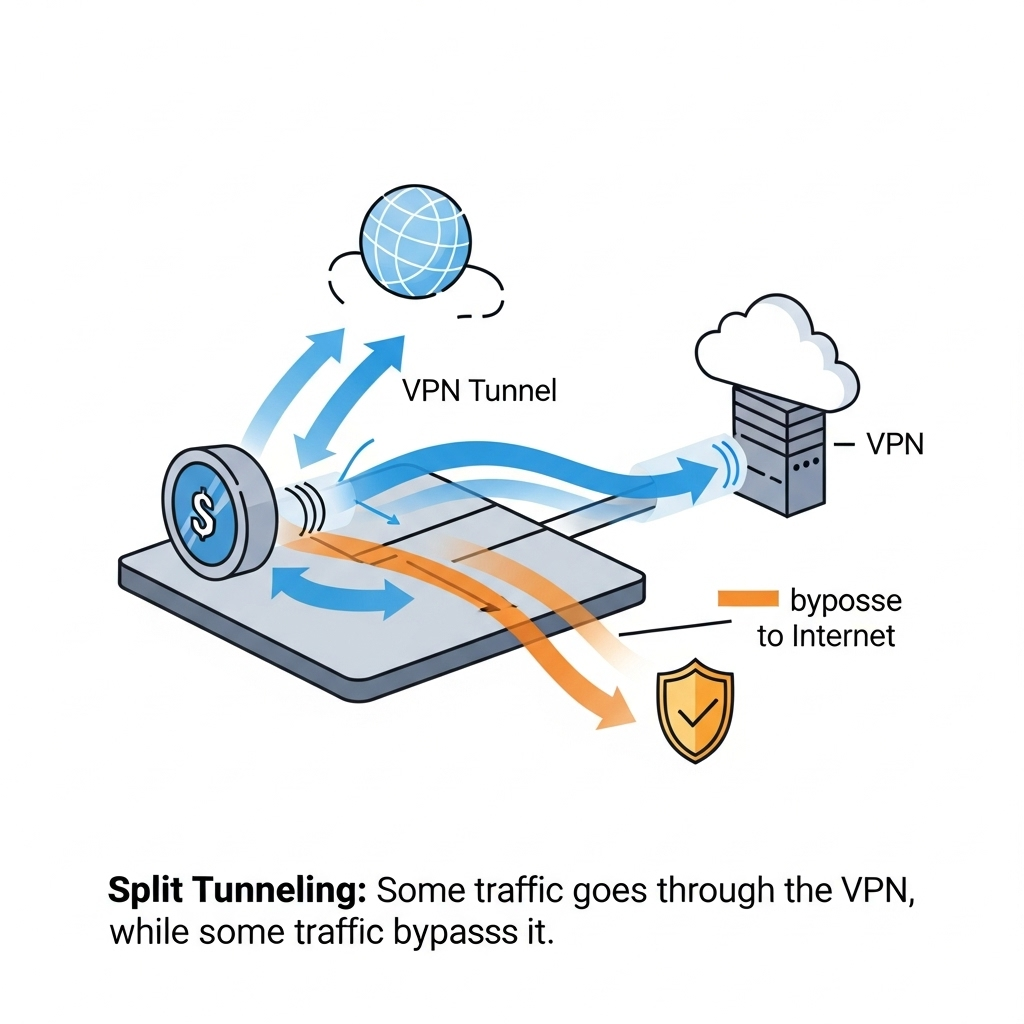
- Strategic Split Tunneling: Most VPNs route all your internet traffic through the encrypted tunnel. Split tunneling VPN offers a different approach, allowing you to selectively route only certain apps or websites through the VPN, while others use your direct internet connection. This is incredibly useful for situations where you need to access local network devices (like a printer) while maintaining your VPN connection for Browse, or if specific banking apps block VPN usage. It provides flexibility without compromising overall security.
Bypassing Tough Blocks with Obfuscated Servers / Stealth VPN: In highly restrictive regions or on networks with advanced VPN detection, standard VPN traffic can be identified and blocked. Obfuscated VPN or stealth VPN servers are designed to disguise your VPN traffic, making it appear as regular internet traffic (like standard HTTPS). This advanced technique helps to bypass VPN blocks in countries with strict internet censorship or on corporate networks.
Understanding DNS Leak Protection: Your device uses DNS (Domain Name System) to translate website names (like https://www.google.com/search?q=google.com) into IP addresses. A DNS leak occurs when your DNS requests bypass the VPN tunnel and go directly to your ISP’s DNS servers, potentially revealing your Browse activity despite being connected to a VPN. Good VPNs include robust DNS leak protection to ensure all DNS queries are routed securely through the encrypted tunnel, protecting your privacy.
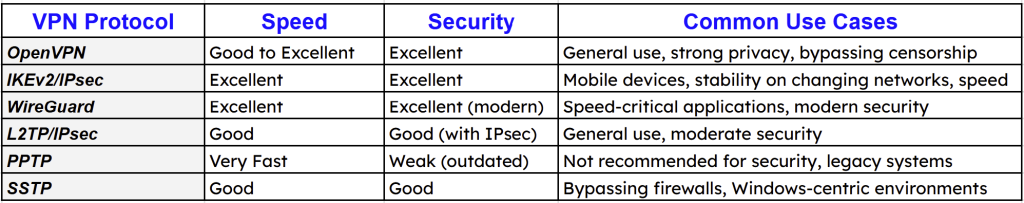
Choosing the Right VPN Protocol: Not all VPN protocols are created equal. Understanding the differences between WireGuard vs OpenVPN vs. IKEv2/IPSec is crucial for optimizing your experience.
WireGuard: Known for its cutting-edge speed, modern cryptography, and lightweight code. Ideal for fast Browse, streaming, and gaming where performance is paramount.
OpenVPN: A highly versatile, open-source protocol known for its strong security and wide compatibility. Often preferred for maximum security and stability.
IKEv2/IPSec: Offers good speed and reliability, particularly strong for mobile devices as it handles network changes gracefully. Choosing the right VPN protocol impacts your security, speed, and overall connection stability.
Enhanced Anonymity with Multi-Hop / Double VPN: For those seeking the highest level of anonymity, some VPNs offer a double VPN or multi-hop VPN feature. This routes your internet traffic through two (or more) VPN servers in different locations, encrypting it multiple times. While this can slow down your connection, it significantly enhances your anonymity, making it extremely difficult to trace your online activity.
Built-in Ad & Malware Blockers: Many premium VPN services now integrate network-level ad and malware blockers. These features filter out intrusive advertisements and block access to known malicious websites, enhancing your Browse speed, reducing data usage, and providing an additional layer of security against cyber threats.
Choosing & Maintaining Your VPN: Best Practices for Longevity
The effectiveness of your online privacy strategy hinges on selecting a reliable VPN and consistently adhering to best practices.
The Crucial No-Logs Policy: The most critical factor when choosing a VPN is its no-logs VPN policy. This means the provider does not collect, store, or share your Browse history, connection logs, IP addresses, or any other identifiable activity data. Look for providers that have undergone independent audited VPN services to verify their claims. This transparency is paramount.
Understanding Server Network & Speed: A VPN’s performance is often linked to its server network. A large, geographically diverse VPN server network provides more options for bypassing geo-restrictions and can lead to better speeds by allowing you to connect to less congested servers closer to your physical location. While some speed loss is inevitable with encryption, a good VPN will minimize it.
Reliable Customer Support: Even the most tech-savvy users can encounter issues. Choose a VPN provider with responsive, knowledgeable 24/7 customer support. This ensures you can get help quickly when troubleshooting connection problems or configuring advanced features.
The Importance of Regular Updates: Cyber threats constantly evolve, and so too must your defenses. Always keep your VPN software updates, operating system, and all other applications up-to-date. Updates often include critical security patches that address newly discovered vulnerabilities, protecting you from emerging threats.
Avoiding “Free” VPNs: While tempting, most “free” VPN services come with significant hidden costs. Many engage in data logging, sell user data to third parties, inject ads, or offer weak encryption. For genuine digital protection, investing in a reputable paid VPN service is essential. Free VPNs often compromise the very privacy they claim to offer.
Basic Troubleshooting Tips: If you experience slow VPN speed fix or connection drops, try these common troubleshooting steps:
Switch to a different server (especially one closer to your physical location).
Experiment with different VPN protocols (WireGuard for speed, OpenVPN for stability).
Restart your VPN application, router, and device.
Check your internet connection without the VPN.
In 2025, navigating the digital landscape demands more than just casual awareness; it requires a proactive, multi-layered approach to online privacy strategies. A VPN is an incredibly powerful tool, but its true strength is unlocked when you understand and utilize its advanced features, and when you combine it with complementary privacy-focused tools and vigilant best practices.
Don’t settle for baseline protection. It’s time to go beyond the basics, master your digital tools, and make informed choices about your secure web Browse. By integrating advanced VPN features with a suite of privacy-enhancing applications and maintaining diligent security habits, you can build a robust digital protection strategy that empowers you to browse, communicate, and interact online with unprecedented confidence and anonymity.
Your journey to a more private, secure, and free online experience starts now. Take control of your digital footprint and browse with confidence!



