Beyond the Invisible Eye: How to Avoid Websites Tracking Your Moves in 2025
In 2025, the internet is an indispensable part of our daily lives, a vast landscape for communication, commerce, and information. Yet, beneath its seamless surface lies an intricate web of invisible trackers, relentlessly monitoring our every digital move. From the moment you land on a website, algorithms begin to record your clicks, scroll patterns, time spent on pages, and even the unique characteristics of your device. This constant surveillance, often executed without explicit consent or clear understanding, fuels targeted advertising, influences online experiences, and builds comprehensive profiles that reveal more about you than you might imagine.
The era of simple cookie blocking is largely behind us. Modern website tracking techniques have evolved, becoming far more sophisticated and pervasive, making it increasingly challenging to maintain online privacy. This article will expose the latest methods websites use to follow your every digital step and, crucially, provide you with the most effective, cutting-edge strategies and tools to regain control, fortify your digital footprint, and browse the web with genuine peace of mind.
Meta Description: Go beyond basic VPN usage. Discover advanced features, complementary privacy tools, and expert tips to truly secure your digital life and maximize online anonymity in today’s interconnected world.
Understanding the Invisible Web: How Websites Track You
To combat tracking effectively, it’s essential to understand the methods websites deploy to collect your data. In 2025, these tactics extend far beyond the basic cookie.
Cookies: The Original Trackers (and Their Evolution)
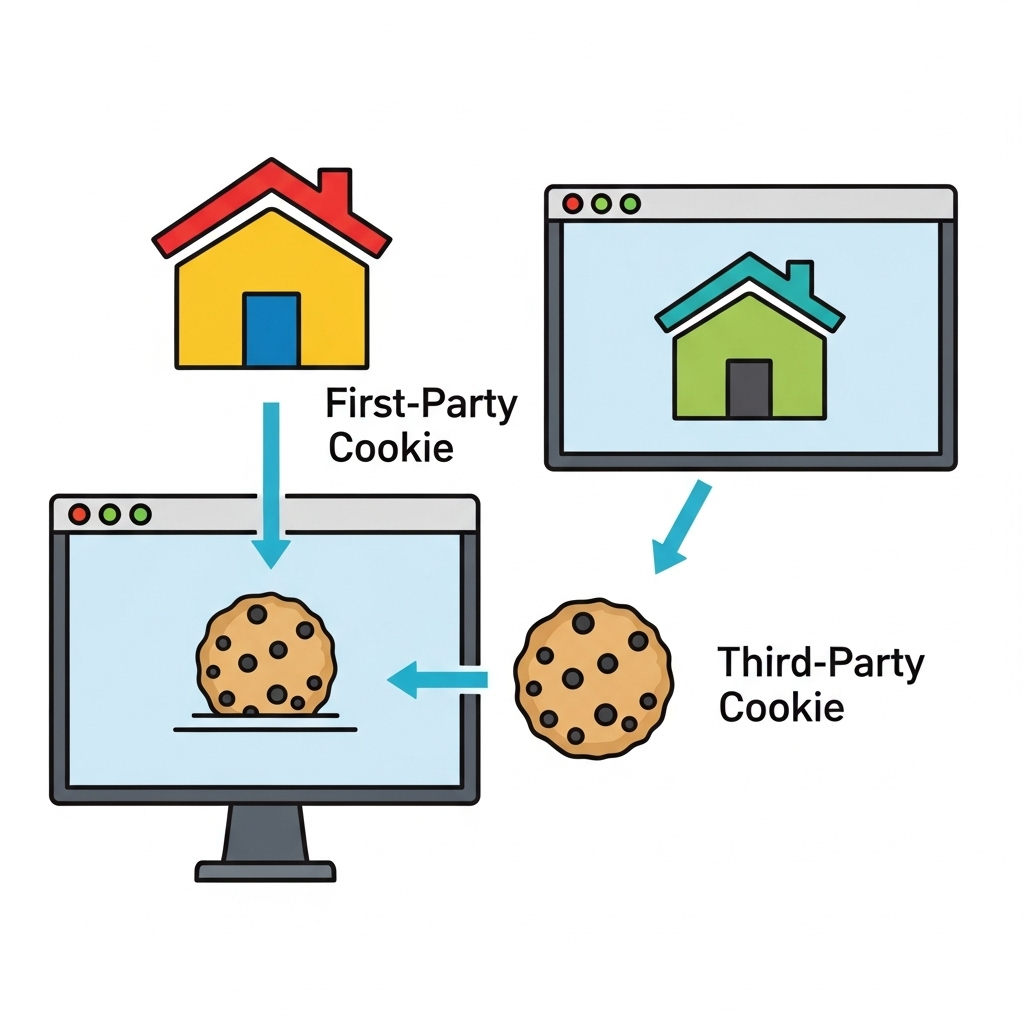
First-Party Cookies: These are legitimate small text files placed by the website you visit. They help remember your preferences, keep you logged in, or recall items in your shopping cart. Generally benign and necessary for site functionality.
Third-Party Cookies: Historically, these were the primary culprits for cross-site tracking. Placed by domains other than the one you’re visiting (e.g., ad networks, analytics providers), they allowed trackers to follow you across multiple websites. While browsers are increasingly phasing these out by 2025, their legacy paved the way for more advanced methods.
- Beyond Cookies: The Rise of Browser Fingerprinting
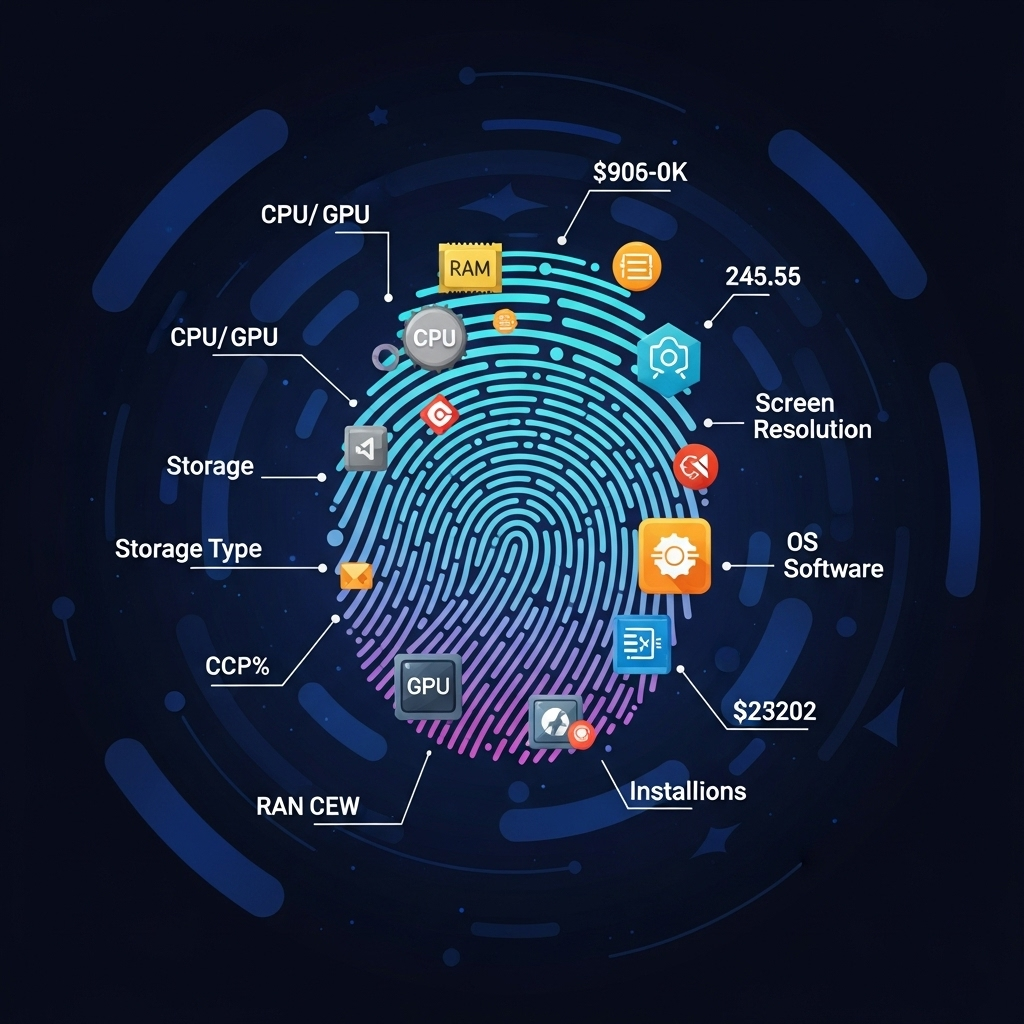
What it is: This is one of the most insidious tracking methods. Instead of storing a file, websites collect a unique “fingerprint” of your device based on its specific characteristics: your browser version, operating system, installed fonts, screen resolution, active plugins, language settings, graphics card, audio context, and even subtle variations in how your browser renders images (Canvas and WebGL fingerprinting).
How it works: Even if you delete cookies or use private Browse, the combination of these unique attributes can identify you with remarkable accuracy across different websites, acting like a unique identifier for your device.
- Pixels, Beacons, and Script-Based Tracking
Invisible Trackers: Tiny, often transparent, 1×1 pixel images (tracking pixels or web beacons) embedded on websites or in emails. When loaded, they send data back to a server, confirming you viewed content or opened an email.
JavaScript & Analytics: Extensive use of JavaScript code by analytics services (like Google Analytics, Adobe Analytics) to track every interaction: clicks, scrolls, mouse movements, time on page, form submissions, and even dynamic content interactions. This builds a detailed behavioral profile.
Key Phrase: tracking pixels, web beacons, JavaScript tracking, website analytics privacy.
Local Storage & Supercookies
Persistent Data: Beyond traditional cookies, browsers offer other ways for websites to store data (e.g., Local Storage, Session Storage, IndexedDB). These can be used to store identifiers that are harder to delete than cookies, sometimes acting as “supercookies” to re-identify you even after cookie clearing.
Browser-Based Defenses: Fortifying Your Digital Frontier
Your web browser is your primary interface with the internet, making it the first and most crucial line of defense against tracking. Configuring it properly and using the right tools can make a significant difference.
Mastering Browser Privacy Settings
Default Protections: Most modern browsers (Firefox, Chrome, Edge, Safari) offer built-in privacy settings. Learn to access and configure them to their strictest levels.
Blocking Third-Party Cookies: Ensure this is enabled by default. While third-party cookies are fading, this remains a fundamental protection.
“Do Not Track” (DNT) Signals: While not legally binding or universally respected, enabling DNT sends a signal to websites that you prefer not to be tracked.
Enhanced Tracking Protection (Firefox): Leverage Firefox’s built-in “Strict” mode for comprehensive tracking and fingerprinting protection.
Privacy-Focused Browsers: Built for Stealth
Brave Browser: Known for its integrated ad and tracker blocker (Brave Shields) that works out-of-the-box. It also offers strong fingerprinting protection by randomizing certain browser attributes. It’s a solid choice for ease of use and immediate privacy gains.
Mozilla Firefox: A highly customizable open-source option. With the right extensions and configuration (like “Strict” Enhanced Tracking Protection), Firefox can be hardened into a formidable privacy browser.
DuckDuckGo Browser: Offers a dedicated browser (for desktop and mobile) that automatically blocks most third-party trackers, enforces HTTPS, and includes a “Fire Button” to instantly clear Browse data.
LibreWolf: A community-driven, privacy-focused fork of Firefox designed to remove telemetry, enhance security, and include better default privacy settings without extensive tweaking.
Tor Browser: While slower, Tor Browser provides the highest level of anonymity by routing traffic through multiple relays and is specifically designed to combat browser fingerprinting by standardizing user configurations. It’s ideal for highly sensitive Browse.
- Essential Browser Extensions for Tracking Prevention
uBlock Origin: A highly efficient and widely recommended open-source ad and content blocker that also blocks a vast array of trackers.
Privacy Badger (EFF): Learns to identify and block invisible trackers that violate user consent by analyzing their behavior.
HTTPS Everywhere (EFF): Automatically ensures your browser connects to websites using the more secure HTTPS protocol whenever available, encrypting your communication.
Cookie AutoDelete: Automatically deletes cookies when you close a tab, preventing websites from tracking your activities across sessions.
ClearURLs: Automatically removes tracking elements from URLs, ensuring cleaner and more private links.
Network-Level & Behavioral Defenses: Beyond the Browser
While browser-based solutions are powerful, a comprehensive strategy against tracking extends to your network and your online habits.
The Role of a VPN in Hiding Your IP Address
IP Masking: A Virtual Private Network (VPN) encrypts your internet traffic and routes it through a server in a location of your choice, effectively masking your real IP address.
Limitations: While a VPN hides your IP (a key tracking identifier), it doesn’t prevent browser fingerprinting or cookies on its own. It’s a foundational layer, not a complete solution.
Suggestion: Maximizing VPN Benefits & Advanced Online Privacy: A Deep Dive for the Discerning Web User.
DNS-Level Ad & Tracker Blocking
Custom DNS: Services like NextDNS or AdGuard DNS can block ads, trackers, and malicious domains at the DNS level across all devices on your network.
Network-Wide Protection: This is powerful because it applies protection to all devices (smart TVs, IoT devices, gaming consoles) connected to your network, not just devices with browser extensions.
Conscious Data Hygiene & Online Behavior
Limit Information Sharing: Be mindful of the personal information you voluntarily share on social media, online forums, and websites. Less shared means less data to track.
Social Media Privacy Settings: Regularly review and tighten privacy settings on all social media platforms to limit data collection and sharing with third parties.
Email Aliases & Temporary Emails: Use services that provide email aliases (e.g., ProtonMail, SimpleLogin, DuckDuckGo Email Protection) or temporary email addresses for non-essential sign-ups to prevent your primary inbox from being flooded with trackers and spam.
Careful with Account Logins: Be wary of using “Login with Google/Facebook” buttons on third-party sites, as this often shares more data than you intend.
Evading ISP Throttling & Data Monitoring: Your Internet Service Provider (ISP) acts as the gateway to the internet, meaning they can see your unencrypted online activities. Some ISPs log your Browse history, and in certain regions, they might even throttle your bandwidth for specific services (e.g., streaming, gaming) to manage network traffic. When you use a VPN, your internet traffic is encrypted, rendering it unreadable to your ISP. This not only prevents them from monitoring your activities but also makes it significantly harder for them to prevent ISP tracking or selectively ISP throttling VPN your connection based on the content you’re accessing. You regain control over your bandwidth and privacy.
Enhanced Torrenting/P2P Safety & Privacy: Peer-to-peer (P2P) file sharing, often associated with torrenting, carries inherent privacy and legal risks if done without proper protection. Your IP address is visible to everyone in the swarm, potentially exposing you to unwanted attention from copyright holders or malicious entities. A VPN becomes crucial for secure torrenting, as it hides your true IP address, making your activity anonymous and significantly reducing privacy and legal concerns during file sharing.
Potentially Saving Money on Online Shopping & Flights: Did you know that prices for flights, hotels, and even some online subscriptions can vary based on your geographical location? Airlines and e-commerce sites sometimes use dynamic pricing. By using a VPN to change your virtual location, you can sometimes discover different pricing tiers, potentially leading to significant online shopping discounts or VPN for cheaper flights. It’s a clever trick for the savvy shopper.
The Ongoing Battle: Adapt and Evolve
The fight against online tracking is a continuous process. Trackers are constantly evolving, finding new ways to identify users as older methods are blocked. Staying ahead requires vigilance and adaptability.
Regular Software Updates: Always keep your operating system, web browser, and all security-related extensions updated. Updates often include critical patches against new tracking methods and vulnerabilities.
Consent Management Fatigue & Skepticism: Many websites bombard users with elaborate cookie consent banners. Learn to understand these, look for “Reject All” or granular control options, and remember that simply closing the banner often implies consent. Be skeptical of vague or misleading language.
The Future of Tracking: AI and Contextual Ads: As third-party cookies fade, expect a rise in contextual advertising (ads based on the content of the page you’re viewing, rather than your past behavior) and AI-driven behavioral analysis that doesn’t rely on traditional identifiers. Your best defense will remain a layered approach to data minimization.
In 2025, navigating the internet without leaving an extensive digital trail requires conscious effort and the right tools. The days of simple cookie deletion being enough are long gone, replaced by sophisticated tracking techniques like browser fingerprinting. However, by adopting a proactive, multi-layered strategy, you can significantly reclaim your online privacy.
Empower yourself by mastering your browser’s privacy settings, leveraging privacy-focused browsers and extensions, and integrating network-level defenses. Combine these technical measures with smart digital footprint management and informed online behavior. Your internet experience doesn’t have to be a constant surveillance operation.
Take control of your website tracking prevention today. Start implementing these strategies, explore the tools discussed, and embrace a more private and secure online existence. Your digital freedom is worth protecting!


